Streamline Crypto Key Management
Top Notch Technology
Across all industries the requirements for managing cryptographic keys are becoming ever-more complex. Ensuring that the right key is in the right place at the right time is mandated by many organisations, i.e. major card payment scheme providers. This is a complicated requirement as most businesses need to manage an ever-increasing number of keys, while reducing the risk of internal and external fraud, as well as keeping costs at a minimum.
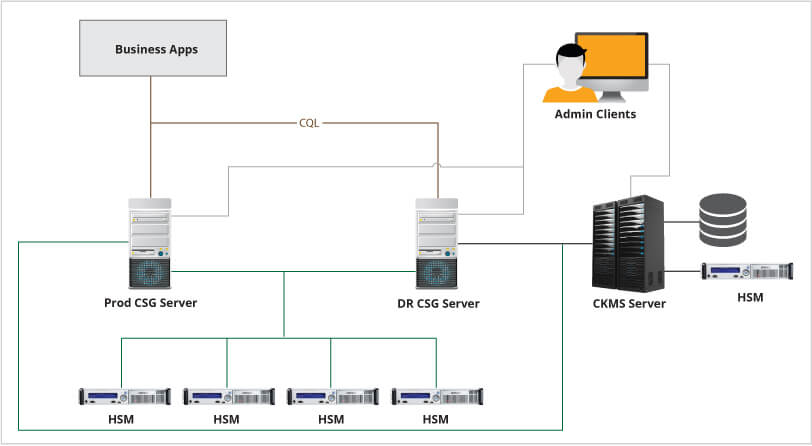
The Crypto Key Management System (CKMS) streamlines administration and reduces costs associated with traditional key management. Through its flexible and automated protocols, CKMS gives users the flexibility to manage a very large number of keys – throughout their entire life cycle – without drowning in work. Using Cryptomathic CKMS, administrators can uniformly and centrally manage the life cycle of all cryptographic keys across a range of encryption platforms.
Crypto Key Management System

*Automated key distribution and updating
*Centralised life cycle key management
*Compliance
Authorities: FIPS, Internal audit, PCI, Payment schemes and S/O
Domains: Physical (e.g. tamper) & logical security (crypto/SW/system design)
*Configurable role-based access
*Flexible key attributes eliminate paperwork
*High availability and scalability
*Searchable tamper evident audit log
*Support for all major HSM brands
*Trusted path using secure PIN pads
-Non-Smart Chip Based
-Self Definable Security Algorithms
-Smart Chip Based
-Multi Levels Access Right Management
-HID Driverless
-User-define security password
-Secure Communication

Key Management solution Brochure
Crypto As A Service

-Non-Smart Chip Based
-Self Definable Security Algorithms
-Smart Chip Based
-Multi Levels Access Right Management
-HID Driverless
-User-define security password
-Secure Communication

SecureDongle Brochure
Crypto Service Gateway
It benefits the smallest of applications, yet scales effortlessly to deliver crypto to the entire enterprise. Discover huge cost and time savings by doing crypto the right way.

CSG’s managed encryption technology addresses a common crypto headache – ensuring encrypted data can be safely decrypted at a later date, even if the original key has been replaced. This technique is ideally suited for long-term storage of encrypted data within a business database, for example. Managed encryption is an optional feature that can be made available to any application using CSG. Managed encryption provides confidentiality, authenticity and integrity (while normal encryption only offers the first of these). This means CSG can ensure the data hasn’t been modified while it was stored. The encrypted data returned by CSG contains a pointer to the key used to perform the encryption. Even if the encryption key is updated, CSG retains access to the old key and can use it to decrypt historical data. Support is also provided for updating old encrypted data to use a newer key.
Tokenization
Tokenization is a common technique for protecting sensitive data, such as PANs, as they pass through business systems. The original data is replaced with a token of the same length, using a reversible process.
CSG offers tokenization as a basic crypto function available to any application. The tokenization process is customisable and can allow parts of the data to pass through un-changed (e.g. the last four digits of the PAN). A configurable mixture of format-preserving encryption and database storage is used to produce the token values.
For those concerned with PCI-DSS, tokenization may provide a way to bring systems out of scope for audits. For more information on PCI-DSS compliance with CSG, please refer to PCI-DSS topic paper
Secure PIN Translation
Secure PIN translation is the process of changing the key that encrypts a PIN, without exposing the PIN data in server memory. This operation is commonly needed in payment systems, where the PIN must travel through different systems which use different zone-related keys.
CSG supports PIN translation using our secure code execution (SCE) technology, which is a vendor-neutral approach to executing code within an HSM. The PIN translation function supports a variety of standard PIN block formats.
-Non-Smart Chip Based
-Self Definable Security Algorithms
-Smart Chip Based
-Multi Levels Access Right Management
-HID Driverless
-User-define security password
-Secure Communication

SecureDongle Brochure
Case Studies
National Cyber Security Agency (NACSA) & Securemetric Berhad
Lazada Group’s Transition from EJBCA Community
Philippine Clearing House implemented PKI-In-A-Box to secure their clearing system
Universiti Utara Malaysia Entrusted Securemetric’s Microsoft Expertise
Turnkey customized EJBCA Enterprise for Vietnam Government Information Security Commission
Badan Siber Dan Sandi Negara upgraded to EJBCA Enterprise







